Bug Bounty
Security of the platform is our highest priority. All smart contracts and off-chain code (i.e. most of the code within the across-protocol repository) are within scope and are publicly verifiable. Security researchers are eligible for a bug bounty for reporting undiscovered vulnerabilities.
Bounty Program
We encourage the community to audit our open source code; we also encourage the responsible disclosure of any issues. The bug bounty program is intended to recognize the value of working with the community of independent security researchers and sets out our definition of good faith in the context of finding and reporting vulnerabilities, as well as what you can expect from us in return.
Across offers substantial rewards for discoveries that can prevent the loss of assets, the freezing of assets, or harm to users.
To be eligible a bounty, a bug must have not been previously known by the Across team or publicly disclosed by anyone. All Across smart contracts and interactions (including bots and front end code) are in scope.
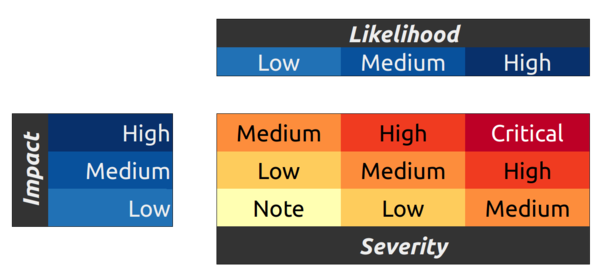
The amount of compensation will vary depending on bug severity. Reward amounts typically correspond to severity in the following manner. The reward currency can be discussed on a case by case basis.
Low
$250
Medium
$1,000
High
$10,000
Critical
up to $1,000,000
Severity is calculated according to the OWASP risk rating model based on Impact and Likelihood.
Submissions
Please email your submissions to [email protected].
The submission must include clear and concise steps to reproduce the discovered vulnerability. The following layout of the bug bounty report is encouraged:
Description: Describe at a high level the bug with links to problematic code
Attack: Detailed instructions for exploiting the bug
Mitigation: How to resolve the bug
Suggested risk rating: The recommended severity of this bug
Terms & Conditions
The same terms and conditions from the UMA bug bounty program apply here.
Last updated